This news disappoints me as I love Android for its apps and UI. However, Researchers from North Carolina State University have demonstrated how Android Apps can access your private data. Android is an Open source OS and manufacturers can modify or personalize it to be used on their devices. There are some flaws in the software that these licensees add to their devices and these flaws open up ways to third part apps which enable them access your private data such as record your calls, send SMS, access your location, photos and a lot more.
ALSO SEE: Android Users’ Private Data can be Hacked [ALERT]
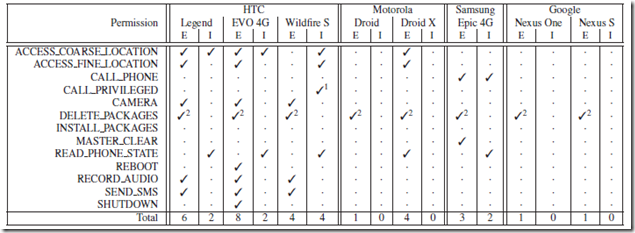
As a total, there are 13 security vulnerabilities which have been tested on 8 phones from leading manufacturers like Google, Samsung HTC and Motorola out of which HTC Evo 4G has 8 positive results which is the maximum.
How Does It Happen?
When you install an app on your Android device, you are prompted to allow the app to access your data which is mentioned on the screen. According to this test conducted by the Researchers, apps can easily circumvent the permission-based security model. The pdf paper from them says:
Android provides a permission-based security model that requires each application to explicitly request permissions before it can be installed to run.
Your phone contains data like current (or past) geo-location information about the user [3], phone call logs of placed and received calls, an address book with various contact information, as well as cached emails and photos taken with the built-in camera which can be found in the cache folder even after deleting.
Phones Tested
The following phones have been tested using Woodpecker prototype to uncover two types of capability leaks – Explicit and Implicit leaks. Explicit capability leaks allow an app to successfully access certain permissions by exploiting some publicly-accessible interfaces or services without actually requesting these permissions by itself. Implicit capability leaks allow the same, but instead of exploiting some public interfaces or services, permit an app to acquire or “inherit” permissions from another app with the same signing key (presumably by the same author)
|
Vendor |
Model |
Android version |
|
HTC |
Legend |
2.1-update1 |
|
Motorola |
Droid |
2.2.2 |
|
Samsung |
Epic 4G |
2.1-update1 |
|
|
Nexus One |
2.3.3 |
Vulnerabilities Found
As mentioned earlier, there are 13 in total out of which HTC EVO 4G shows a maximum of 8. The results are shown in the image below.
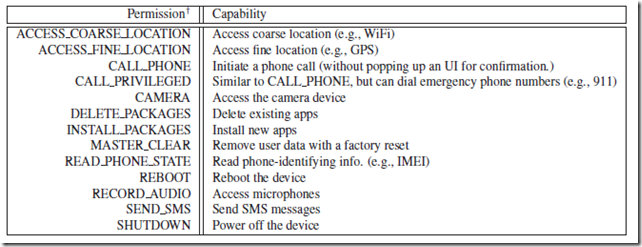
Now the image below helps you understand the permissions better along with their capabalities.
Conclusion
Being and Android user you can not actually do anything regarding this but ye, the manufacturers or Android can surely do something to overcome these security breaches. Apple uses a vetting process through which each third-party app must be scrutinized before it will be made available in the app store. After installing an app, Apple’s iOS platform will prompt the user to approve the use of some functions at run-time, upon their first access. I hope Android does something similar or to curb the implicit capability leaks, Android should change the way apps interact with each other.
What do you think could be a possible solution to it?